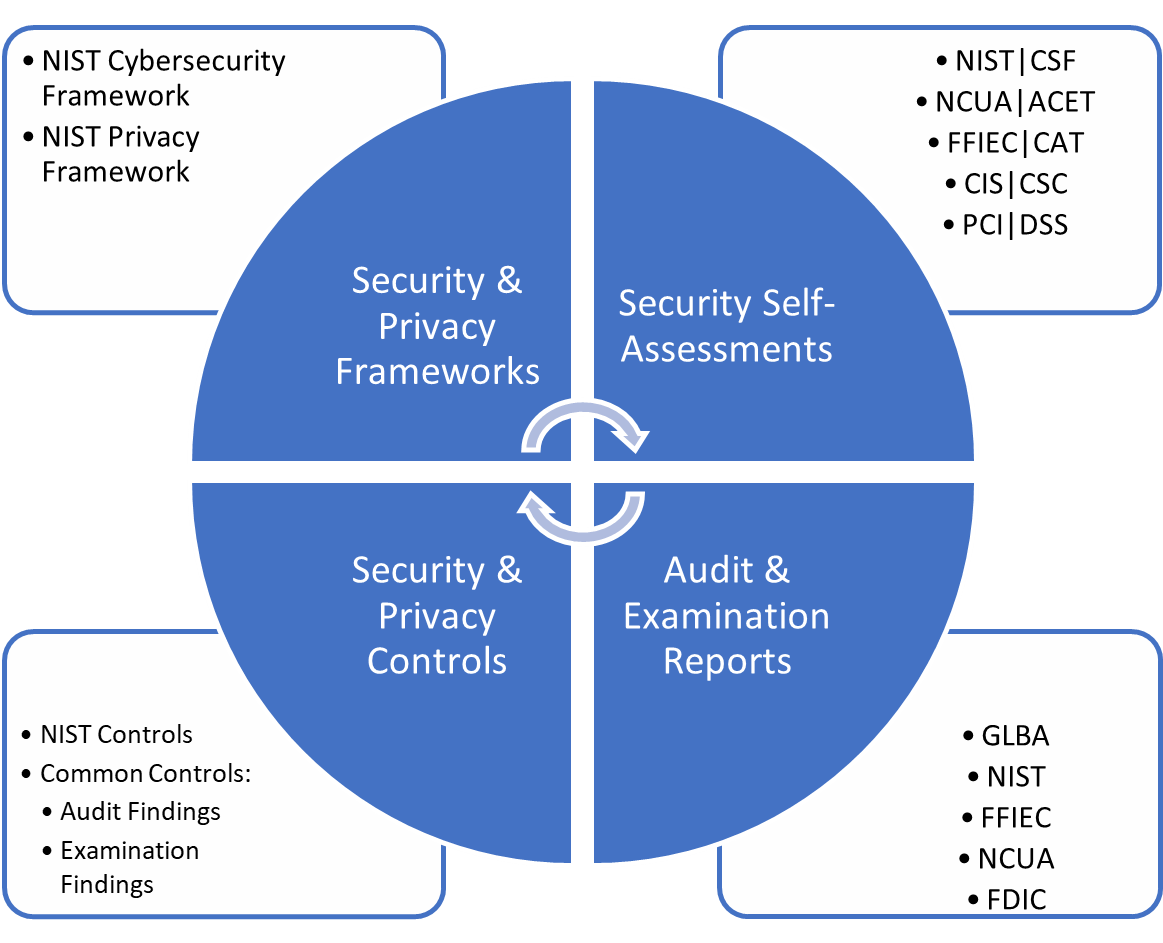
Information Security Program
In response to financial institution customers and in compliance with FFIEC, FDIC and NCUA guidance, Trumbull Security Services LLC has developed a NIST Cybersecurity Framework 2.0 based Information Security Program and embedded the FFIEC|CAT within it to ensure a comprehensive risk-based information security program that is both light weight, effective and tailored towards financial institutions. All security and privacy controls are implemented using NIST SP 800-53r5 Policies, Controls and Procedures to ensure they are properly designed and implemented.
NIST Cybersecurity Framework (CSF)
The Framework provides a common language for understanding, managing, and expressing cybersecurity risk to internal and external stakeholders. It can be used to help identify and prioritize actions for reducing cybersecurity risk, and it is a tool for aligning policy, business, and technological approaches to managing that risk. The framework is used to manage cybersecurity risk across entire organizations, and it is focused on the delivery of critical services within an organization.
CSF Framework Core
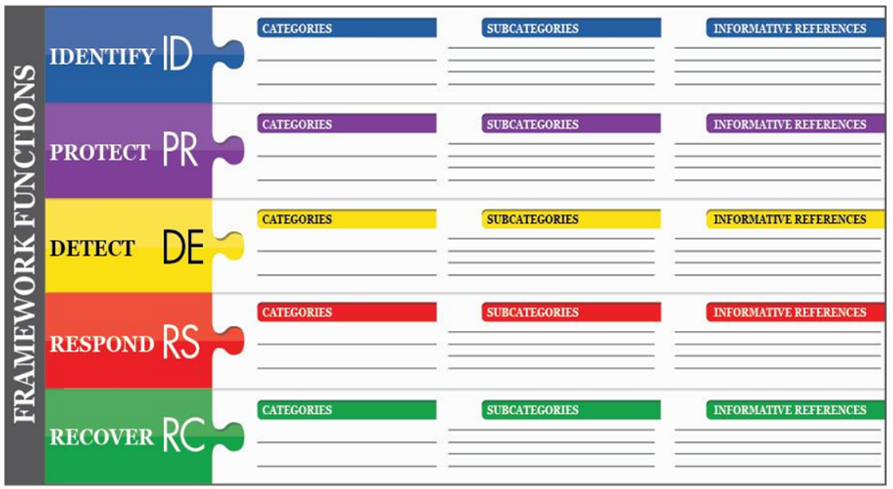
The Framework Core provides a set of activities to achieve specific cybersecurity outcomes, and references examples of guidance to achieve those outcomes. The Core is not a checklist of actions to perform. It presents key cybersecurity outcomes identified by stakeholders as helpful in managing cybersecurity risk. The Core comprises four elements: Functions, Categories, Subcategories, and Informative References, depicted below:
The Framework Core elements work together as follows:
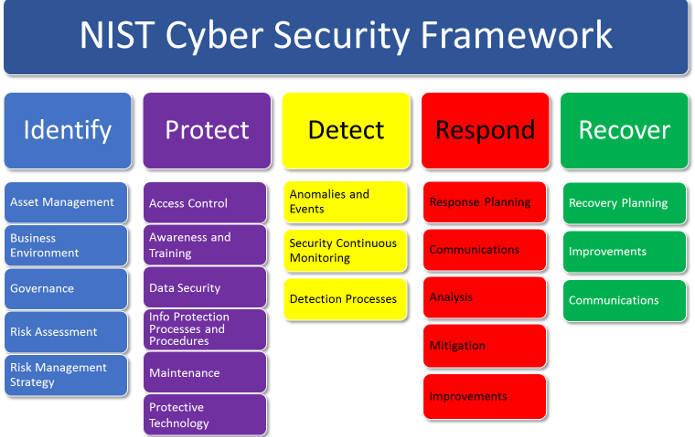
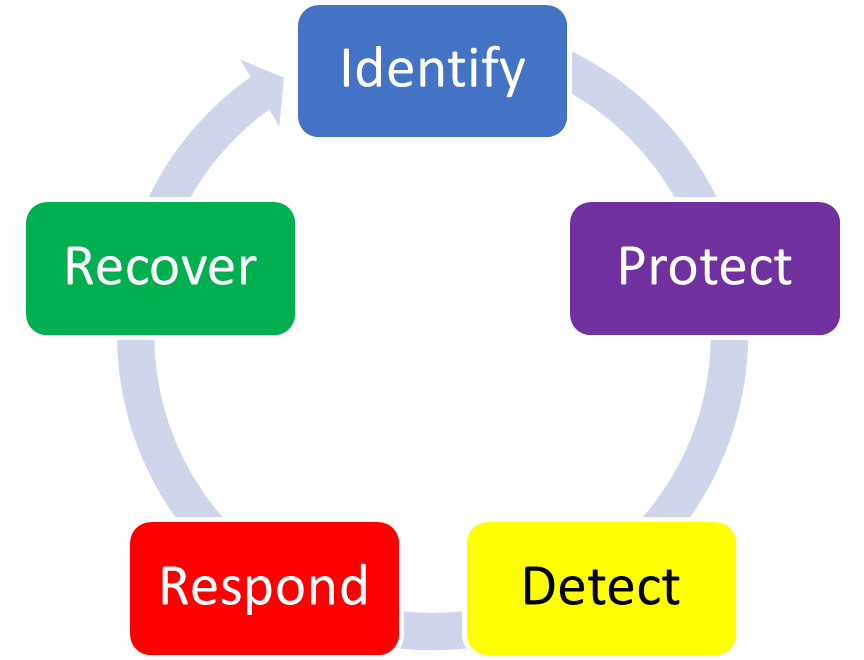
- Functions organize basic cybersecurity activities at their highest level. These Functions are Identify, Protect, Detect, Respond, and Recover. They aid an organization in expressing its management of cybersecurity risk by organizing information, enabling risk management decisions, addressing threats, and improving by learning from previous activities. The Functions also align with existing methodologies for incident management and help show the impact of investments in cybersecurity. For example, investments in planning and exercises support timely response and recovery actions, resulting in reduced impact to the delivery of services.
- Categories are the subdivisions of a Function into groups of cybersecurity outcomes closely tied to programmatic needs and particular activities. Examples of Categories include “Asset Management,” “Identity Management and Access Control,” and “Detection Processes,” etc.
- Subcategories further divide a Category into specific outcomes of technical and/or management activities. They provide a set of results that, while not exhaustive, help support achievement of the outcomes in each Category. Examples of Subcategories include “External information systems are catalogued,” “Data-at-rest is protected,” and “Notifications from detection systems are investigated.”
- Informative References are specific sections of standards, guidelines, and practices common among critical infrastructure sectors that illustrate a method to achieve the outcomes associated with each Subcategory. For financial institutions, this is where the FFIEC|CAT controls are referenced to ensure that the NIST CSF Subcategories are oriented towards addressing the unique security and privacy challenges facing financial institutions.
The five Framework Core Functions are defined below. These Functions are not intended to form a serial path or lead to a static desired end state. Rather, the Functions should be performed concurrently and continuously to form an operational culture that addresses the dynamic cybersecurity risk.
- Identify – Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. The activities in the Identify Function are foundational for effective use of the Framework. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs. Examples of outcome Categories within this Function include Asset Management; Business Environment; Governance; Risk Assessment; and Risk Management Strategy.
- Protect – Develop and implement appropriate safeguards to ensure delivery of critical services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event. Examples of outcome Categories within this Function include Identity Management and Access Control; Awareness and Training; Data Security; Information Protection Processes and Procedures; Maintenance; and Protective Technology.
- Detect – Develop and implement appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables timely discovery of cybersecurity events. Examples of outcome Categories within this Function include Anomalies and Events; Security Continuous Monitoring; and Detection Processes.
- Respond – Develop and implement appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident. Examples of outcome Categories within this Function include Response Planning; Communications; Analysis; Mitigation; and Improvements.
- Recover – Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident. Examples of outcome Categories within this Function include Recovery Planning; Improvements; and Communications.
Information Security Program Preparedness
Beyond the development and implementation of the information security program FDIC, NCUA and FFIEC strongly encourage financial institutions to continuously perform cybersecurity self-assessments to evaluate the readiness and coverage of their program.
To simplify and automate the assessment process, the IRM webapp has mapped each of the assessment statements to NIST SP 800-53r5 Policies, Controls and Procedures that best satisfy the credit union response(s) based on the implementation status of each control. In this manner, the assessments are automatically updated as the credit union implements the information security program, incrementally and over time.
For Credit Unions & Banks, the following self-assessment tools include:
- FFIEC Cybersecurity Assessment Tool ( FFIEC|CAT ) In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council (FFIEC) developed the Cybersecurity Assessment Tool (Assessment) to help institutions identify their risks and determine their cybersecurity preparedness. The Assessment provides a repeatable and measurable process for financial institutions to measure their cybersecurity preparedness over time.
- FFIEC Cyber Security Assessment
- FFIEC Inherent Risk Profile
- FFIEC Cybersecurity Maturity
- FFIEC Cybersecurity Framework
- NCUA Automated Cybersecurity Evaluation Toolbox (NCUA|ACET) application provides credit unions the capability to conduct a maturity assessment aligned with the Federal Financial Information Council’s (FFIEC) Cybersecurity Assessment Tool . ACET is comprised of 494 detailed evaluation elements spanning five information security domains:
- NCUA | ACET Inherent Risk Profile
- NCUA | ACET Maturity Detail
- NCUA | ACET Domain 1: Cyber Risk Management & Oversight
- NCUA | ACET Domain 2: Threat Intelligence & Collaboration
- NCUA | ACET Domain 3: Cybersecurity Controls
- NCUA | ACET Domain 4: External Dependency Management
- NCUA | ACET Domain 5: Cyber Incident Management and Resilience
- Center for Internet Security Critical Security Controls (CIS|CSC) . Formerly the SANS Critical Security Controls (SANS Top 20) these are now officially called the 18 CIS Critical Security Controls (CIS Controls):
- CIS Control 1: Inventory and Control of Enterprise Assets
- CIS Control 2: Inventory and Control of Software Assets
- CIS Control 3: Data Protection
- CIS Control 4: Secure Configuration of Enterprise Assets and Software
- CIS Control 5: Account Management
- CIS Control 6: Access Control Management
- CIS Control 7: Continuous Vulnerability Management
- CIS Control 8: Audit Log Management
- CIS Control 9: Email and Web Browser Protections
- CIS Control 10: Malware Defenses
- CIS Control 11: Data Recovery
- CIS Control 12: Network Infrastructure Management
- CIS Control 13: Network Monitoring and Defense
- CIS Control 14: Security Awareness and Skills Training
- CIS Control 15: Service Provider Management
- CIS Control 16: Application Software Security
- CIS Control 17: Incident Response Management
- CIS Control 18: Penetration Testing
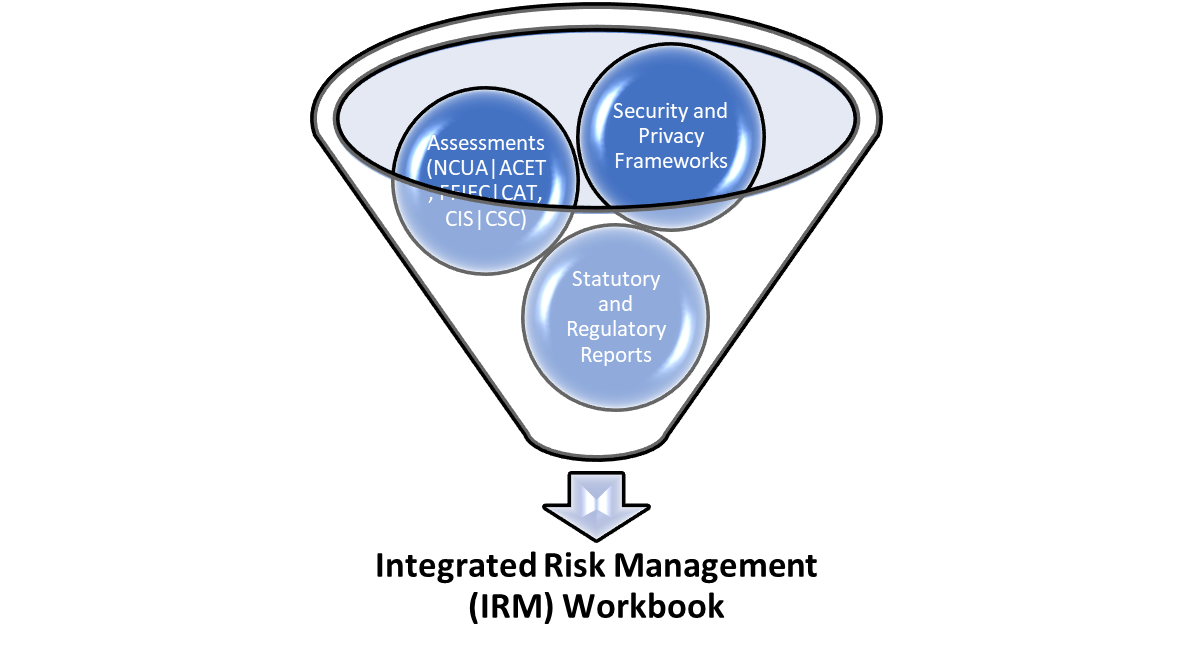
Integrated Risk Management (IRM)
To help manage the complexity and accuracy of required reports needed to satisfy information security audits and NCUA examinations, the IRM webapp provides an Integrated Risk Management (IRM) capability that encapsulates all of the information security and privacy frameworks (NIST|CSF, NIST|PF), all of the self-assessments (NCUA|ACET, FDIC|SSP, FFIEC|CAT, CIS|CSC, etc.), as well as the numerous reports needed for statutory and regulatory requirements (GLBA 12 CFR Part 748, NIST|CSF, NIST|PF, NCUA|ACET, FFIEC|CAT, CIS|CSC, Plan of Action and Milestones, Audit and Examination Findings, etc.).
Risk management is recognized as an essential tool to tackle the inevitable uncertainty associated with business projects at all levels. But it frequently fails to meet expectations, with projects continuing to run late, run over budget and/or underperforming.
The evident disconnect which often occurs between strategic vision and tactical project delivery typically arises from poorly defined project objectives and inadequate attention to the proactive management of risks that could affect those objectives.
In consideration of the aforementioned challenges the webapp has approached IRM with focus on incorporating all statutory and regulatory requirements (GLBA, FFIEC, FDIC, NCUA, PCI, and State Privacy Statutes) and correlating those with the requisite policies, controls and procedures specified by industry standard information security (NIST|CSF) and privacy (NIST|PF) frameworks.
Information Security and Privacy Policies
For Credit Unions the Cybersecurity Framework is comprised of twenty-two (22) specific NIST policies implemented utilizing two-hundred-thirty-five (235) well-defined NIST controls and procedures. Each of the policies documented below notes which NIST SP 800-53 r5 controls were used to implement any given policy, the controls themselves and their implementation status are documented separately in a complementary document ‘Credit Union - Information Security and Privacy Controls and Procedures.’
- ACCESS CONTROL (AC) POLICY: implements Role-based Access Controls (RBAC) for all company defined positions and roles and implements Least-Privilege Administrative Models to ensure that accounts are established and maintained to limit access to only what is required to perform a given job function.
- AWARENESS AND TRAINING (AT) POLICY: Information security awareness is an evolving part of information security that focuses on raising consciousness regarding potential risks of the rapidly evolving forms of information and the rapidly evolving threats to that information which target human behavior. The goal of Information security awareness is to make employees aware that they are susceptible to the opportunities and challenges in the threat landscape, change human risk behaviors and enhance a secure culture.
- AUDIT AND ACCOUNTABILITY (AU) POLICY: Audit and accountability are important elements of any security program to ensure that the policy mandated by statutory and regulatory compliance are in place, continuously monitored and enforced. Specifically the policy addresses Event Logging, Content of Audit Records, Limit Personally Identifiable Information Elements, Audit Log Storage Capacity, Response to Audit Logging Process Failures, Audit Record Review, Analysis, and Reporting, Audit Record Reduction and Report Generation, Time Stamps, Audit Record Retention, Audit Record Generation, Monitoring for Information Disclosure, Session Audit, Cross-organizational Audit Logging and Disassociability.
- ASSESSMENT, AUTHORIZATION, AND MONITORING (CA) POLICY: Develop a security and privacy assessment plan that describes the scope of the assessment including security and privacy controls and control enhancements under assessment, assessment procedures to be used to determine control effectiveness and assessment environment, assessment team, and assessment roles and responsibilities. Ensure the assessment plan is reviewed and approved by the Board of Directors Authorized Audit Committee as the authorizing official prior to conducting the assessment and assess the security and privacy controls in the system and its environment of operation annually to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting established security and privacy requirements.
- CONFIGURATION MANAGEMENT (CM) POLICY: Establishes a Confidential Unclassified Information System Security Plan ( CUI-SSP ) for each system that documents software usage restrictions, enforces any user-installed software permitted, uniquely identifies each system, establishes a baseline configuration for both hardware and software, maintains a history of change control, provides a security and privacy impact analysis for any changes applied, provides a separate test environment to test the changes applied, document and enforce access restrictions for changes, documents configuration settings, implement least-privileges and least-functionality, and maintain a complete system component inventory
- CONTINGENCY PLANNING (CP) POLICY: Develop a contingency plan for the system that identifies essential missions and business functions and associated contingency requirements, provides recovery objectives, restoration priorities, and metrics; and addresses contingency roles, responsibilities, assigned individuals with contact information, maintains essential missions and business functions despite a system disruption, compromise, or failure and plans for eventual, full system restoration without deterioration of the security and privacy controls originally planned and implemented, is reviewed and approved by Management and Departmental Heads, and distributes copies of the contingency plan to key contingency personnel (identified by role) and elements, and coordinates contingency planning activities with incident handling activities
- IDENTIFICATION AND AUTHENTICATION (IA) POLICY: shall implement Multifactor Authentication (MFA) for all systems, assets, resources and personnel to ensure that the credentials being used uniquely identify the authorized individual user.
- INDIVIDUAL PARTICIPATION (IP) POLICY: The information systems and technology resources covered by this policy are intended for business purposes. Unauthorized personal use of the credit union’s systems and resources is prohibited. However, certain provisions for limited personal use (for example, research or purchases on the Internet, or writing a personal letter using credit union-licensed software, etc.) may be allowed if such activities are legal, are not disruptive and are performed during non-work time. Employees must seek approval from their manager prior to engaging in any personal use of credit union resources. Time should not be wasted on non-company business.
- INCIDENT RESPONSE (IR) POLICY: Establishes policy and procedures for the effective implementation of the controls and control enhancements for information security incident response and helps provide security and privacy assurance. Specifically, the policy addresses Incident Response Training, Breach Training, Incident Response Testing, Incident Handling, Incident Monitoring, Incident Reporting, Incident Response Plan, and Information Spillage Response.
- MAINTENANCE (MA) POLICY: Ensures that the system maintenance procedures implement the system maintenance policy and controls; and develop, document, and implement remediation actions for violations of the maintenance policy. utilizes and maintains formal change control process and forms requiring authorization by Chief Information Officer (CIO) prior to any changes to production user and/or server systems. Scheduled maintenance change control windows are monthly and occur on the 2nd week of each month.
- MEDIA PROTECTION (MP) POLICY: This control addresses the establishment of policy and procedures for the effective implementation of the controls and control enhancements to address media access, media marking, media storage, media transport, media sanitization, media use, and media downgrading.
- PRIVACY AUTHORIZATION (PA) POLICY: Trust has always been the foundation of a credit union’s relationship with their members. Because members trust us with their financial and other personal information, is committed to respect privacy and safeguard that information. To preserve member trust, we pledge to protect privacy by adhering to the practices, establishes, documents, and disseminates to Management and Departmental Heads, a privacy authorization policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among entities, and compliance; and is consistent with applicable laws, Executive Orders, directives, regulations, policies, standards, and guidelines; and procedures to facilitate the implementation of the privacy authorization policy and the associated privacy authorization controls.
- PHYSICAL AND ENVIRONMENTAL PROTECTION (PE) POLICY: Policy addresses a broad range of physical and environmental protection requirements for Physical Access Authorizations, Access by Position or Role, Two Forms of Identification, Restrict Unescorted Access, System Access, Facility and Lockable, Tamper Protection, Physical Barriers, Access Control Vestibules, Access Control for Transmission, Access Control for Output Devices, Monitoring Physical Access, Intrusion Alarms and Surveillance Equipment, Automated Intrusion Recognition and Responses, Video Surveillance Monitoring Physical Access to Systems, Visitor Access Records, Automated Records Maintenance and Review, Limit Personally Identifiable Information Elements, , Power Equipment and Cabling, Redundant Cabling, Automatic Voltage Controls, Emergency Shutoff, Emergency , Alternate Power Supply, Minimal Operational Capability, Emergency Lighting, Fire Protection Detection Systems, Automatic Activation and Notification, Fire Suppression Systems‚ Fire Control Inspections, Environmental Automatic Controls, Monitoring with Alarms and Notifications, Water Damage, Delivery and Removal, Alternate Work Site, Information Leakage, Asset Monitoring and Tracking , Electromagnetic Pulse Protection, Component Marking, and Facility Location.
- PLANNING (PL) POLICY: Develop, document, and disseminate to Management and Departmental Heads security and privacy planning policies that address purpose, scope, roles, responsibilities, management commitment, coordination among entities, and compliance; and are consistent with applicable laws, Executive Orders, directives, regulations, policies, standards, and guidelines; and procedures to facilitate the implementation of System Security and Privacy Plans, Rules of Behavior, and Security and Privacy Architectures.
- PROGRAM MANAGEMENT (PM) POLICY: This policy addresses the Information Security Program Plan, Information Security Program Leadership Role(s), Information Security and Privacy Resources, Plan of Action and Milestones Process, System, Inventory of Personally Identifiable Information , Measures of Performance, Enterprise Architecture, Offloading, Critical Infrastructure Plan, Risk Management Strategy, Authorization Process, Mission and Business Process Definition, Insider Threat, Security and Privacy Workforce, Testing, Training, and Monitoring, Security and Privacy Groups and Associations, Threat Awareness Program, Privacy Program Plan, Privacy Program Leadership Role, Dissemination of Privacy Program Information, Accounting of Disclosures, Personally Identifiable Information Quality Management, Data Governance Body, Complaint Management, Privacy Reporting, Risk Framing, Risk Management Program Leadership Roles, Supply Chain Risk Management Strategy, Continuous Monitoring Strategy.
- PERSONNEL SECURITY (PS) POLICY: Establishes the Personnel Security Policy and Procedures, and addresses requirements for Personnel Screening, Personnel Termination, Personnel Transfer, Access Agreements, External Personnel Security, Personnel Sanctions, and Position Descriptions.
- PERSONALLY IDENTIFIABLE INFORMATION PROCESSING AND TRANSPARENCY (PT) POLICY: Policy and Procedures for PII, Authority to Process Personally Identifiable Information, Data Tagging, Automation, Personally Identifiable Information Processing Purposes, Consent, Tailored Consent, Just-in-time Consent, Revocation of Consent, Privacy Notice, Just-in-time Notice, Privacy Act Statements, System of Records Notice, Routine Uses, System of Records Notice Exemption Rules, Specific Categories of Personally Identifiable Information, Social Security Numbers, First Amendment Information Computer and Matching Requirements.
- RISK ASSESSMENT (RA) POLICY: This control addresses the establishment of policy and procedures for the effective implementation of the controls and control enhancements for Risk Assessments. The policy addresses Security Categorization, Impact-level Prioritization, Risk Assessments, Vulnerability Monitoring and Scanning, Risk Response(s), Privacy Impact Assessments, Criticality Analysis, and Threat Hunting.
- SYSTEM AND SERVICES ACQUISITION (SA) POLICY: Credit Union management will require its service providers to maintain compliance with the Gramm-Leach-Bliley Act. As part of the Credit Union’s efforts, management will Develop, document, and disseminate to Management and Departmental Heads a system and services acquisition policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among entities, and compliance, is consistent with applicable laws, Executive Orders, directives, regulations, policies, standards, and guidelines, and procedures to facilitate the implementation of the system and services acquisition policy and the associated system and services acquisition controls that address Policy and Procedures Allocation of Resources , System Development Life Cycle, Acquisition Process, System Documentation, Security and Privacy Engineering Principles, Clear Abstractions, Least Common Mechanism, Modularity and Layering, Partially Ordered Dependencies, Efficiently Mediated Access, Minimized Sharing, Reduced Complexity, Secure Evolvability, Trusted Components, Hierarchical Trust, Inverse Modification Threshold, Hierarchical Protection, Minimized Security Elements, Least Privilege, Predicate Permission, Self-reliant Trustworthiness, Secure Distributed Composition, Trusted Communications Channels, Continuous Protection, Secure Metadata Management, Self-analysis, Accountability and Traceability, Secure Defaults, Secure Failure and Recovery, Economic Security, Performance Security, Human Factored Security, Acceptable Security, Repeatable and Documented Procedures, Procedural Rigor, Secure System Modification, Sufficient Documentation, Minimization, External System Services, Developer Configuration Management, Developer Testing and Evaluation, Static Code Analysis, Development Process, Standards, and Tools, Developer-provided Training, Developer Security and Privacy Architecture and Design, Customized Development of Critical Components, and Developer Screening.
- SYSTEM AND COMMUNICATIONS PROTECTION (SC) POLICY: The following system and communications protection controls shall be applied to -managed system assets, including those managed by external service partners including, Policy and Procedures, Separation of System and User Functionality, Disassociability, Information in Shared System Resources, Denial-of-service Protection, Resource Availability, Boundary Protection, Personally Identifiable Information, Transmission Confidentiality and Integrity, Network Disconnect, Trusted Path, Cryptographic Key Establishment and Management, Cryptographic Protection, Collaborative Computing Devices and Applications, Transmission of Security and Privacy Attributes, Integrity Verification, Public Key Infrastructure Certificates, Mobile Code, Secure Name/Address Resolution Service (Authoritative Source), Secure Name/Address Resolution Service (Recursive or Caching Resolver), Architecture and Provisioning for Name/Address Resolution Service, Session Authenticity, Unique System-generated Session Identifiers, Protection of Information at Rest, Heterogeneity, Covert Channel Analysis, System Partitioning, Distributed Processing and Storage, Out-of-band Channels, Operations Security, Process Isolation, Wireless Link Protection, Port and I/O Device Access, Notice of Collection, Collection Minimization, Usage Restrictions, Detonation Chambers, System Time Synchronization, Synchronization with Authoritative, Secondary Authoritative Time Source, Cross Domain Policy Enforcement, Alternate Communications Paths, Sensor Relocation, Dynamic Relocation of Sensors or Monitoring Capabilities, Hardware-enforced Separation and Policy Enforcement, Software-enforced Separation and Policy Enforcement, and Hardware-based Protection.
- SYSTEM AND INFORMATION INTEGRITY (SI) POLICY: Develop, document, and disseminate to – Security Steering Committee a system and information integrity policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among entities, and compliance, and is consistent with applicable laws, Executive Orders, directives, regulations, policies, standards, and guidelines, and procedures to facilitate the implementation of the system and information integrity policy and the associated system and information integrity controls including Policy and Procedures, Flaw Remediation, Malicious Code Protection, System Monitoring, Security Alerts, Advisories, and Directives, Security and Privacy Function Verification, Software, Firmware, and Information Integrity, Spam Protection, Information Input Validation, Information Management and Retention, Limit Personally Identifiable Information Elements, Minimize Personally Identifiable Information in Testing, Training, and Research, Information Disposal, Predictable Failure Prevention, Non-persistence, Memory Protection, Fail-safe Procedures, Personally Identifiable Information Quality Operations, Automation Support, Data Tags, Notice of Correction or Deletion, De-identification, and Motivated Intruder.
- SUPPLY CHAIN RISK MANAGEMENT (SR) POLICY: Supply chain risk management policy and procedures address the controls in the SR family as well as supply chain-related controls in other families that are implemented within systems and organizations. The risk management strategy is an important factor in establishing such policies and procedures such as Policy and Procedures, Supply Chain Risk Management Plan, Supply Chain Controls and Processes, Provenance, Acquisition Strategies, Tools, and Methods, Supplier Assessments and Reviews, Notification Agreements, Tamper Resistance and Detection, Inspection of Systems or Components, and Component Disposal.
Additionally, there are six (6) FFIEC/NCUA required policies to address internet-based applications and services.
- CLOUD COMPUTING (CL) POLICY: Use of Cloud Computing services must be formally authorized by operating CIO and COO in accordance with the Credit Union risk management framework and certification processes, formal vendor due diligence performed, and Cloud Computing project manager appointed. The designated Cloud Computing project manager must coordinate planning with the operating CIO early in the planning process to avoid unnecessary problems later in the planning and acquisition lifecycle.
- INTERNET AND MOBILE BANKING (IM) POLICY: In an effort to maintain competitive advantage and provide a high level of personalized service to our members, the Credit Union offers Internet banking services through its Web site, www.DortFCU.org and mobile banking via apps designed for various portable devices. The Credit Union views the Internet and mobile banking services as additional delivery channels, not to supplant traditional banking, but to complement it. This policy communicates the strategic, operational and risk management considerations that are presented by Internet and mobile banking and outlines the Credit Union’s policy to manage this technology.
- WEBSITE (WS) POLICY: The Credit Union maintains a Web site that is hosted. All content is developed and maintained by Credit Union. The Credit Union offers the following services electronically: Online Banking, Bill Pay, Loan Application.
- VISITOR (VS) POLICY: Access to nonpublic areas within the Credit Union will be restricted by doors and/or gates that are locked at all times. A logbook will be maintained to document all visitors entering restricted areas at the Credit Union. "Visitors" include vendors, repair technicians, janitorial help, and any other non-office employees. The logbook will record the date, name of visitor and visitor's company, time of arrival and departure, purpose of visit, signature of visitor, and name of Credit Union employee assigned to escort the visitor. The visitor's identity and authorization will be verified by telephone to the visitor's company or office unless both the visitor and the reason for the visit are known to Credit Union personnel. To avoid possible hostage situations, the visitor will not be told of this verification procedure. An assigned employee will accompany the visitor at all times while the visitor is in restricted areas of the Credit Union. The CIO or branch manager may make exceptions to this rule. Such exceptions will be noted in the visitor logbook.
- SOCIAL MEDIA (SM) POLICY: The Credit Union may use social media in a variety of ways including advertising and marketing, providing incentives, facilitating applications for new accounts, inviting feedback from the public, and engaging with existing and potential members, for example by receiving and responding to complaints, or providing loan pricing. Training and guidance will be provided to employees regarding the official use of social media - that is, when employees communicate officially on behalf of the Credit Union. For example, if an employee is communicating with a member regarding a loan product through an approved social media channel, policies and procedures will be developed to include steps to ensure the member is receiving all of the required disclosures.
- E-STATEMENT (ES) POLICY: The Credit Union offers electronic periodic statements, or “e-statements,” to its members in an effort to reduce postage and printing costs, as well as the cost of paper and envelopes; the savings of which can then be passed on to the membership. In addition, online communication with members enables the Credit Union to build or enhance member relationships by providing the Credit Union with the ability to target or personalize its marketing efforts. Members will be encouraged to sign up for e-statements, as they will receive their statements and other electronic promotional material much sooner than if the Credit Union sent this information through the postal system. Before a member may receive e-statements, the Credit Union must ensure compliance with Section 101(c) of the Electronic Signatures in Global and National Commerce Act (E-SIGN).
Information Security Program Documents
The Information Security Program is comprised of the following documents:
- Information Security and Privacy Policies
- Information Security Program
- Information Privacy Program
- Information Security and Privacy Controls and Procedures
- Integrated Risk Management Reports
- Incident Response Plan
- Supply Chain Risk Management Plan
- Vulnerability Management Program
- Exception Management Program
Policy Review and Reports to the Board of Directors
Statutory and regulatory compliance requires that the Information Security Policies and Program be reviewed annually to evaluate and adjust, as appropriate, in light of any relevant changes in technology, the sensitivity of our member’s information, internal or external threats to information, and our own changing business arrangements.
At least annually the policies and program documents shall be reviewed and approved by the Board. The Board’s review will include discussion of the risk assessment, risk management and control decisions, service provider arrangements, results of testing, any security breaches or violations and management’s response and recommendations for changes in the information security program.
Adjustments to the Information Security Policies and Program
Adjustments will be made to the policies and program as deemed necessary by management and the Board of Directors during periodic review of the Information Security Program. When changes in technology or business processes impact on the Information Security Program, management will review the changes and assess the related risk that will be introduced. Then, appropriate controls will be implemented to mitigate identified risks.
Page last updated: Tue 04 June 2024